In recent weeks, a new and highly convincing phishing scam has been circulating that pretends to be an Adobe Acrobat “Secure Document” request. At first glance, it looks legitimate — often even coming from a trusted contact’s real email address with their usual signature.
But beneath the surface, it’s a sophisticated attack designed to steal your Microsoft login credentials.
How the Scam Works:
- You receive an email that looks like this:
- Subject line: “Please Review Secure Document” or “Encrypted File Attached”
- Body text: “Kindly review the attached document and get back to me at your earliest convenience.”
- A blue link or button labeled “Review Document”
- The link will direct you to an Adobe Acrobat page.
- It may or may not have a document password listed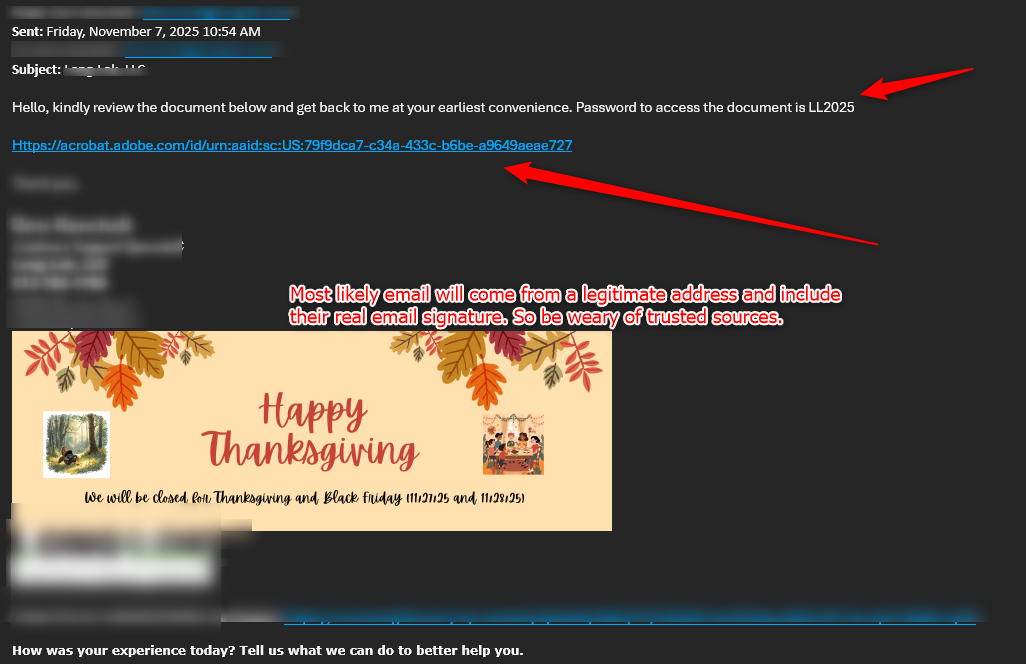
- It then directs you to a legitimate Adobe Acrobat page, with prompts like:
"Please Review"
"Your security is our priority."
"Password required to open this file." [The phishing email may or may not have a password]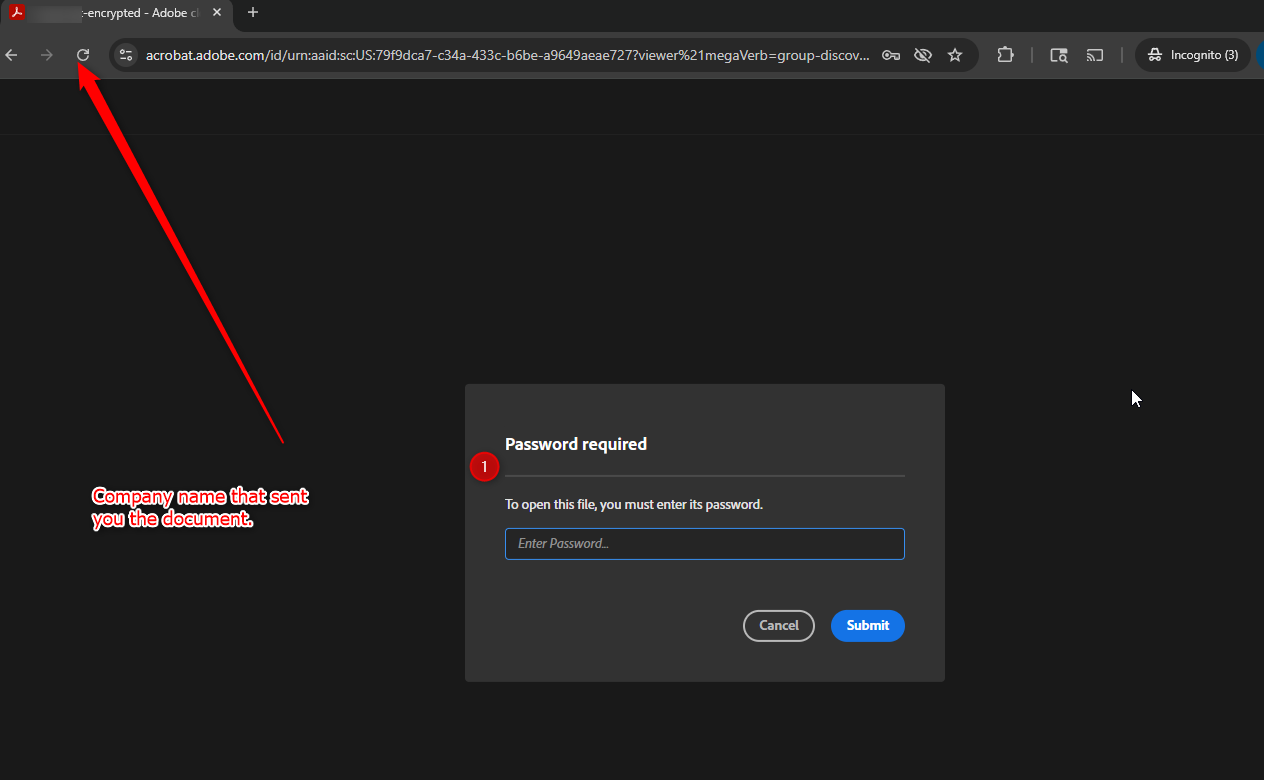
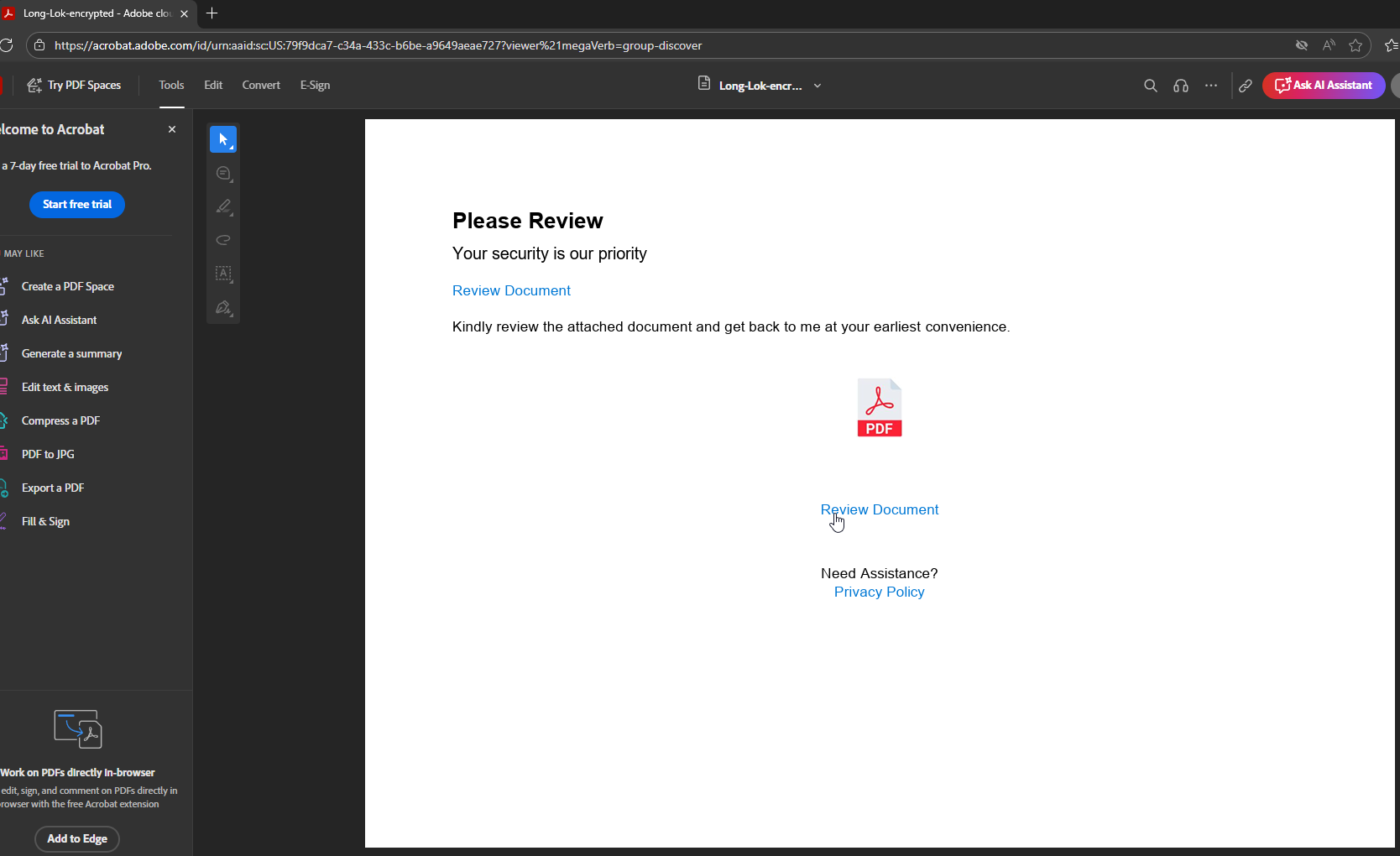
- The document you open is an Adobe PDF, so it will take you to the legitimate acrobat.adobe.com, but this is part of the trick.
Then, when you open the document (either it will open on its own or, if they made it look more legitimate by putting a password in the email for you to use), that is when it directs you to the MALICIOUS LINK. Once you click on "review document" in the PDF, it brings you to a malicious webpage capable of intercepting your Microsoft OAUTH token - a digital key that keeps you logged into your Microsoft 365 account. This is why multi-factor authentication won't save you from this scam.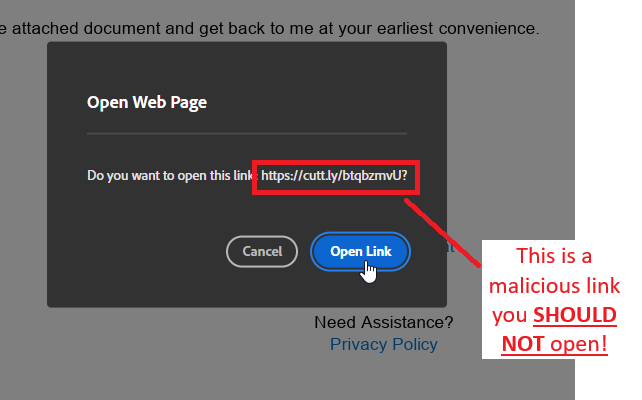
What Makes This Attack So Dangerous:
This phishing technique is token-based, not password-based. That means:
- You don’t have to type your password for your credentials to be stolen (they steal it from the token on your web browser when you tell Microsoft you are working from a "trusted" device). This means your multi-factor authentication set up WILL NOT PROTECT YOU FROM THIS SCAM.
- Once they have your token, they can:
- Send emails as you to your contacts
- Access your OneDrive and Teams data
- Bypass two-factor authentication and most email scanners
Traditional antivirus or spam filters cannot detect this because the attack happens through a legitimate encrypted web session in your browser.
What You Should Do To Stay Protected From This and Similar Attacks:
- Open all document links in a private browser session
- Use InPrivate (Edge) or Incognito (Chrome) when opening links to PDFs — even from known senders. This prevents any stored login tokens from being exposed. - Verify before opening
- If an email seems even slightly suspicious, contact the sender directly using a separate message or call before clicking. - Be cautious with “encrypted” or “secure” document prompts
- If you’re not expecting a document, assume it’s a scam until verified. - Report suspicious messages
- Forward questionable emails to your IT department.
Why Awareness is Key
This campaign’s biggest weapon is trust.
By using familiar email addresses, real company logos, and official-sounding messages, it tricks users into letting their guard down.
That’s why education and awareness are your strongest defense.
At A M Exclusive, we continuously monitor emerging cyber threats like this to help keep your business safe — because we treat your business like it’s our own.
If you think you might have clicked on one of these links:
If you believe you've fallen for a phishing scam or entered your credentials on a suspicious page, immediately reset your password. Contact your IT department or email provider to report the incident and secure your account. You can also contact our team for help.
By staying vigilant and following these simple steps, you can protect yourself from these growing phishing threats.
Stay safe online!



